Vmware Opencl Support
Vmware Opencl Support
David Benjamin discovered that OpenSSL incorrectly handled comparing certificates containing a EDIPartyName name type. A remote attacker could possibly use this issue to cause OpenSSL to crash, resulting in a denial of service. CVEs contained in this USN include: CVE-2020-1971 Affected VMware Products and Versions. Introduction For many reasons, customers periodically enquire about which TLS cipher suites are supported by VMware vSphere. This resource outlines the default TLS settings, as detected experimentally with testssl.sh 3.0.1 using OpenSSL 1.0.2k-dev as delivered as part of that testssl.sh release ('testssl.sh -E host.name.com:443'). VMware's approach accelerates the transition to solutional-computing while preserving existing investments and improving security and control. 2.1.1 VMware OpenSSL FIPS Object Module The VMware OpenSSL FIPS Object Module is a software cryptographic module that is built from the. This VMware product ships with OpenSSL 1.0.1, but it has been confirmed to use OpenSSL in a way that renders it not vulnerable to the OpenSSL Heartbleed issue: VMware vRealize Automation (formerly known as vCloud Automation Center) 5.x; These VMware products that ship with OpenSSL 0.9.8 or 1.0.0 have been confirmed to be unaffected: ESXi/ESX 4.x. The remote VMware ESXi host is affected by multiple vulnerabilities in the OpenSSL third-party library: - A flaw exist in the Elliptic Curve Digital Signature Algorithm (ECDSA) implementation due to a failure to insure that certain swap operations have a constant-time behavior. An attacker can exploit this to obtain the ECDSA nonces by using a.
Openssl Vmware Tools
Tableau public tool. These instructions provide a sample for how to set a self-signed certificate using OpenSSL for Integration Broker.
Vmware Opencl
- Create a self-signed certificate for the Integration Broker server.
- Create the ibcerts folder to use as the working directory.
- Create a configuration file using the vi openssl_ext.conf command.
- Copy and paste the following OpenSSL commands into the configuration file.
# openssl x509 extfile params
extensions = extend
[req] # openssl req params
prompt = no
distinguished_name = dn-param
[dn-param] # DN fields
Free tor browser ios. C = US
ST = CA
O = VMware (Dummy Cert)
OU = Horizon Workspace (Dummy Cert)
CN = hostname (Virtual machine hostname where the Integration Broker is installed. )
emailAddress = EMAIL PROTECTED
[extend] # openssl extensions
Game Jam Buildbox Blog Buildbox Forum Buildbox Discord. Report an Issue Request a Feature Contact Support Buildbox Manual API Reference How To/FAQs. Game Jam Buildbox Blog Buildbox Forum Buildbox Discord. Buildbox is a new video game maker that is extremely easy to use. Using this video game software, anyone can design amazing games for mobile, console, and PC. Buildbox discord commands. Game Jam Buildbox Blog Buildbox Forum Buildbox Discord. Report an Issue Request a Feature Contact Support Buildbox Manual API Reference How To/FAQs. Choose a plan and start making games The ultimate game builder with options for every level. Save Money with an Annual Subscription!
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid:always
keyUsage = digitalSignature,keyEncipherment
extendedKeyUsage=serverAuth,clientAuth
[policy] # certificate policy extension data
Note: Type the CN value before you save the file. - Run this command to generate a private key.
- Type the passphrase for server.key, for example, vmware.
- Rename the server.key file to server.key.orig.
- Remove the password associated with the key.
- Copy and paste the following OpenSSL commands into the configuration file.
- Create a CSR (certificate signing request) with the generate key. The server.csr is stored in your working directory.
- Sign the CSR.
The expected output displays.
Signature ok subject=/C=US/ST=CA/O=VMware (Dummy Cert)/OU=Horizon Workspace (Dummy Cert)/CN=w2-hwdog-xa.vmware.com/emailAddress=EMAIL PROTECTED Getting Private key
- Create P12 format.
- Press Enter at the prompt for an export password. The expected output is server.p12 file.
- Move the server.p12 file to the Windows machine where Integration Broker is installed.
- From the Command Prompt, type mmc.
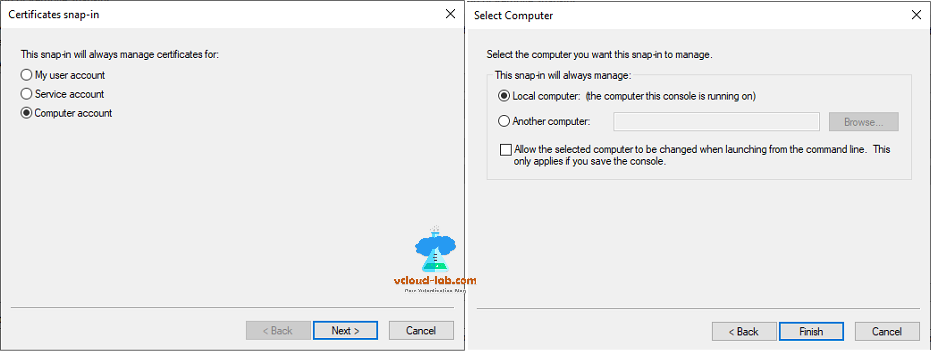
- Click File > Add or Remove Snap-ins.
- In the Snap-in window, click Certificates and click Add.
- Select the Computer account radio button.
- Press Enter at the prompt for an export password.
- Import the certificate into the root and personal store certificates.
- Choose All Files in the dialog.
- Select the server.p12 file.
- Click the Exportable check box.
- Leave the password blank.
- Accept the defaults for the subsequent steps.
- Copy the certificate into the Trusted Root CAs in the same mmc console.
- Verify that the content of the certificate includes these elements.
- Private key
- CN in the subject attribute that matches the Integration Broker Host Name
- Extended key usage attribute with both client and server authentication enabled

